Work Packages
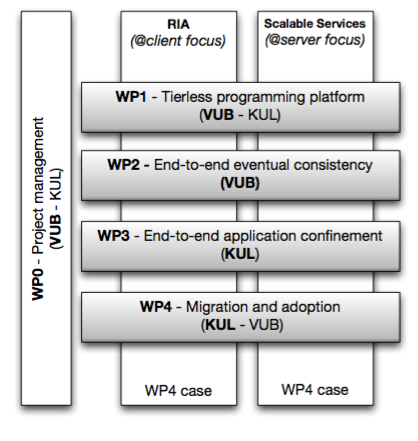
To protect the application assets across the different tiers, we will incept and develop an end-to-end application confinement. This security control will protect the confidentiality and integrity of the application data, as well as access to application-specific APIs. The confinement will provide a foolproof isolation environment to shield the application from other code running outside the application. In addition, access across this isolation boundary will be controlled to guarantee the security invariants of the application. The end-to-end confinement will span the client and the server tier, and will enforce confinement policies expressed as part of the tierless application.
We will explicitly investigate a migration trajectory that enables companies to adopt our results gradually. Existing code bases cannot, and probably should not, be rendered tierless overnight. However, they can benefit from the enabling technologies — provided that they are applied consistently.